Attack surface reduction and other security settings in Windows Pro
Recently I was reading news articles about ransomware attacks, and noticed some remarks from a security specialist on LinkedIn on LSA Protection. This prompted me into doing some research on the subject,
and then I also came across the subject of attack surface reduction.
Just to note, I am not a security specialist, and not even a system administrator, but it is a really interesting subject. So for explanations I refer to the sources I found on the subject.
On the subject of LSA Protection I found the following article Do You Really Know About LSA Protection (RunAsPPL)?
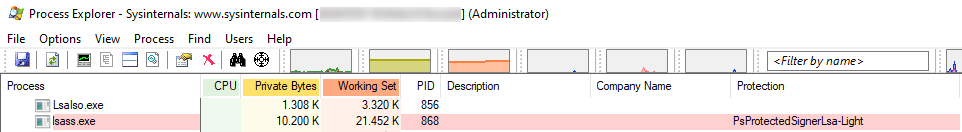
I noticed that on my machine the lsass process was already virtualized in the Lsalso.exe process. You can read about this on Windows 10 Device Guard and Credential Guard Demystified.
To be honest, I wasn't even aware of this. I guess it was on by default, or I switched it on.
As I like to script things, I created small a PowerShell script to switch on LSA Protection:
# Enabling LSA Protection (RunasPPL)
# Run as Administrator
# See:
# https://itm4n.github.io/lsass-runasppl/
$path = "HKLM:\SYSTEM\CurrentControlSet\Control\Lsa"
New-ItemProperty -Path $path -Name "RunAsPPL" -Value 1 -PropertyType DWord
The next thing I stumbled on when looking at this was Attack surface reduction. I found the following articles:
Use attack surface reduction rules to prevent malware infection,
Microsoft Defender Attack Surface Reduction recommendations and
Enable attack surface reduction rules (paragraph on PowerShell)
I also used PowerShell to script these settings, this also was the easiest way to enable this on my Windows Pro machines. For enterprises there are different options for managing these settings.
For now I skipped the 'Use Caution' items mentioned in the recommendations article. I looked up the GUID's in the Attack surface reduction rules reference.
# Attack Surface Reduction
# Run as Administrator
# See:
# https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/attack-surface-reduction
# https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-attack-surface-reduction?view=o365-worldwide#powershell
# https://blog.palantir.com/microsoft-defender-attack-surface-reduction-recommendations-a5c7d41c3cf8
# From the blog, these ID's are marked as: Safe for most environments
# and the ID's with (*) behind the comment are marked as: Environment specific
$arsIds = @(
"3B576869-A4EC-4529-8536-B80A7769E899", # Block Office applications from creating executable content
"7674ba52-37eb-4a4f-a9a1-f0f9a1619a2c", # Block Adobe Reader from creating child processes
"9e6c4e1f-7d60-472f-ba1a-a39ef669e4b2", # Block credential stealing from the Windows local security authority subsystem (lsass.exe)
"b2b3f03d-6a65-4f7b-a9c7-1c7ef74a9ba4", # Block untrusted and unsigned processes that run from USB
"BE9BA2D9-53EA-4CDC-84E5-9B1EEEE46550", # Block executable content from email client and webmail
"D3E037E1-3EB8-44C8-A917-57927947596D", # Block JavaScript or VBScript from launching downloaded executable content
"e6db77e5-3df2-4cf1-b95a-636979351e5b", # Block persistence through WMI event subscription
"D4F940AB-401B-4EFC-AADC-AD5F3C50688A", # Block all Office applications from creating child processes (*)
"75668C1F-73B5-4CF0-BB93-3ECF5CB7CC84", # Block Office applications from injecting code into other processes (*)
"92E97FA1-2EDF-4476-BDD6-9DD0B4DDDC7B", # Block Win32 API calls from Office macros (*)
"5BEB7EFE-FD9A-4556-801D-275E5FFC04CC" # Block execution of potentially obfuscated scripts (*)
)
$arsIds | Foreach {
Add-MpPreference -AttackSurfaceReductionRules_Ids $_ -AttackSurfaceReductionRules_Actions Enabled
}
You might want to start differently, with other settings and/or use Audit (2) or Warn (6) modes first, with the Enabled option I opted for the Block (1) mode.
At last, while looking at my Windows Defender settings, I noticed the 'Microsoft Defender Application Guard'. Please look at:
Microsoft Defender Application Guard overview
for more information on this. To enable this, please look at: Prepare to install Microsoft Defender Application Guard
That's it, I found these subjects really interesting, and having someone pointing to these subjects can really be helpful. Hope you find this a useful help for getting informed about
these important subjects.